Message Keys
– A Security Pass for Messages
1. INTRODUCTION

The purpose of Message Keys is to prevent legitimate messages from being mistaken for Spam – in the same way that a security pass prevents airport employees from being mistaken for terrorists. To continue the analogy, conventional Spam filtering technology is more comparable to the physical barriers, security surveillance, and screening that an airport may employ to keep terrorists out. While these filtering measures are important, their efficiency is improved greatly by the issuing of security passes to legitimate employees – as is the efficiency of a spam filter which utilizes Message Keys to identify legitimate messages. Security Passes are a necessary and important feature of any secure environment, just as Message Keys are to the integrity and reliability of the Internet’s public email system.
Because Message Keys are inserted at the point where the sender acquires the email address, they can provide information to the Spam Filtering Engine that cannot be gained by message inspection. The key can be used to recover information pertaining to how the email address was acquired by the sender, when and where it was acquired, and because each acquisition event is given its own key, a key can be invalidated at any time without affecting other uses of the system – in a similar way to how a security pass can be revoked. Message Keys don’t stop spam, they just stop legitimate messages from being mistaken for Spam.
While attaching a security pass to an employee may be obvious, just how to attach a “security pass” to an email message, without modification to the senders system or the delivery system in between, is not so obvious. Maintaining backwards compatibility with the Internet’s existing systems is the genius of Message Keys and is explained in detail below. While one could easily add a new header to carry the Key, the preservation of such a header through common operations such as; replying, forwarding, and address booking a contact, would require many modifications to the existing infrastructure, specifically with regards to existing email client applications. However, Message Keys uses the email address itself to carry the key, maintaining end to end compatibility with existing systems.
Message Keys is a complementary technology, it works with existing anti-spam technologies to ensure that legitimate messages are not mistaken for spam. All anti-spam solutions can benefit from Message Keys technology. As none of the existing anti-spam technologies are perfect, all of the anti-spam solutions available today can be improved by incorporating Message Keys technology. Whatever their current “false positive rate” – Message Keys can improve it by approximately 90%.
-
The problem
During 2003, Ferris Research estimated that the cost of lost messages to the end user was $3.50 per message. However, unfortunately they did not quantify the cost of a lost message to the ISP, the Spam filter provider, or to the web mail service provider.
While the cost to the end user may be significant1, it is born across hundreds of thousands of users, where as the costs to email service providers is concentrated and born largely by only a few hundred providers. Current user orientated research may have only revealed the tip of the Iceberg. As users experience and sophistication increases, so does user awareness of lost messages, and with that the readiness of a user to move to a more favorable solution. Perhaps over time, given the users existing predisposition to churn, the real cost of lost messages may be a decisive factor in the future viability of service providers in this industry.
From the users perspective, if the objective of today’s Spam filters is to reduce exposure to Spam, then for most users they have failed. This is because whenever a user checks their Spam folder, they are being exposed to all of the Spam – only the folder name is different. Only when a system’s false positive rate is reduced to the point where the user no longer checks their Spam folder, is Spam exposure reduced.
The point is that if the user is routinely checking their Spam folder then the filter is of diminished value, and is more likely to be swapped out for a more promising solution.
Gartner (2003) estimates that 7% of ISP Churn is directly attributed to spam.
So why are users still checking their Spam folders when the anti-spam industry is spouting such low false positive rates? The answer is false positives, false positives2, and the fear of a false positive. While the industrys false positive rates may sounds impressive, the user is more affected by the Lost Message Rate which is not so inspiring.
-
New Term – Lost Message Rate (LMR)
Surprisingly the industry does not appear to have a term for the percentage of legitimate messages that are mistaken for Spam. For the purposes of this paper we will refer to this ratio as the Lost Message Rate.
-
Usage
The Lost Message Rate as an indicator is more reflective of the users experience than that of the internal workings of the Spam filter, and is therefore typically used to answer questions of user behavior such as What is the users tolerance to lost messages? or How does the lost message rate relate to client churn?.
Lost Message Rate can also be used to quantify things that the false positive rate cant, such as a filters false positive effectiveness for different types of messages. For example the lost message rate for first contact messages would be likely to be different to that of newsletters, which would be likely to be different again to that of replies that are a part of an existing conversation.
The term lost message rate can be applied to a class of message to determine a filters effectiveness with a given type of message. On the other hand, the term false positive rate would not be suitable for this purpose as it conveys no knowledge of the proportion of the given class of message within the sample being tested.
-
Different Types of Lost Messages
When considering the cost of a lost message, it is useful to classify the messages in to groups. For the purpose of further discussion, lets tabulate the characteristics of each group.
-
First Contact
As the name suggests, a first contact message is the message of first contact with the protected user from a given sender. Of the different types of lost messages, first contact lost messages are the least likely to be discovered and manually recovered.
First Contact messages often bring new business or new opportunities. Typically the injury to the protected user would be greater and the user would be less tolerant to lost First Contact messages. If discovered, these are the types of lost messages that users remember, that instigate support calls, and that people talk about.
Table 2: First Contact
| Feature | Value |
|---|---|
| Churn Influence | High |
| User Injury | High |
| Avoid-ability | Difficult |
-
Replies
Reply Messages are part of a conversion or the continuation of an existing relationship. They are the easiest lost message to avoid, and bear a high level of user discovery. Fear of this type of lost message is the most common reason for a user to frequent their Spam folder.
Table 3: Replies
| Feature | Value |
|---|---|
| Churn Influence | Medium |
| User Injury | Medium |
| Avoid-ability | Easy |
-
Solicited Bulk Email
 This group includes email publications, Newsletter Subscriptions, Automated Confirmation Messages, Validation and Activation emails, and messages from email based services such as Lyris’ Content Checker3, or Googles Alerts4 service. They are often difficult to avoid as often the same message is sent to multiple users, some of which may incorrectly report the message as Spam. Accordingly, systems that utilize user feedback may suffer heavily from this type of lost message.
This group includes email publications, Newsletter Subscriptions, Automated Confirmation Messages, Validation and Activation emails, and messages from email based services such as Lyris’ Content Checker3, or Googles Alerts4 service. They are often difficult to avoid as often the same message is sent to multiple users, some of which may incorrectly report the message as Spam. Accordingly, systems that utilize user feedback may suffer heavily from this type of lost message.
Table 3: Solicited Bulk Email
| Feature | Value |
|---|---|
| Churn Influence | Annoyance |
| User Injury | Low |
| Avoid-ability | Difficult |
-
Message Keys
Message Keys are a unique code or key that is embedded in to an email address in such a way that it is likely to be retained during normal use of that address, and is therefore available to be extracted at a later date when that email address is used to send an email to the protected user (that owns that email address). It is an important aspect of Message Keys – that the key is preserved in the email address itself, rather than in an additional email header (as in the case of DomainKeys5) or a remote repository (as is the case of Sender Policy Framework6 (SPF) records – which are stored in DNS records). Message Keys work with the existing Internet infrastructure that is in place today, and requires no additional headers or modification to existing third party systems or processes.
-
CaseKeys
CaseKeys are a type of Message Key that use the CAsE of the LeTTerS that make up an email address to embed a unique key into every instance of that email address, whether it is obtained from a web site, a newsgroup posting, or the reply address of an outgoing email. A typical CaseKey might look like this:
joHN.SmiTH@eXamPLE.Com
-
Display Name Annexing
Display Name Annexing (DNA) is a type of Message Key that appends or encodes a unique key within the Display Name portion of the email address. A typical display name key may look something like this:
"John Smith 12345" <john.smith@example.com>
-
Tagged Addressing
Tagged Addressing is appending a key to the local part of an email address via standard plus (or minus) addressing. Tagged addressing is most appropriate for typed-in addresses where the email address is to be published on an off-line medium such as a business card, or is provided over the phone. Tagged Addressing alone is not recommended for use with on-line services due to non-universal compatibility with some email systems and the proliferation of non-RFC compliant email addresses validation routines7. Tagged addressing is only available where the underlying email system supports it. Gmail for example supports plus addressing, while Yahoo! Mail supports minus addressing8.
A typical Plus Addressing key may look something like this:
john.smith+12345@example.com
-
DNA/CaseKey Hybrid
A DNA/CaseKey Hybrid Key is a combination of the first two methods above. It is a DNA key with a CaseKeyed representation of the protected users email address included in both the Display Name part of the email address and the addr-spec address9. It may look like this
"John Smith (joHN.SmiTH@eXamPLE.Com)" joHN.SmiTH@eXamPLE.Com
It is typically automatically inserted in to all instances of the protected users email address in all out-going messages.
-
Tagged Addressing/CaseKey Hybrid
A Tagged Addressing/CaseKey Hybrid Key, as the name suggests is a combination of the Tagged Addressing and CaseKey methods. It is essentially a Tagged Addressing Key that has been CaseKey encoded. It may look like this
joHN.SmiTH+12345@eXamPLE.Com
It is typically manually issued to a user via a user interface for use on web forms. The idea is that if the form does not support tagged addressing then the tag should be removed thereby falling back to the CaseKeyed representation.
-
How Message Keys Work
Message Keys work by providing information to the Spam Filtering Engine on how the email address was acquired by the sender. As mentioned previously, this is achieved by embedding a unique code, or key at the point of email address acquisition, and then checking any incoming messages for a valid key, thereby ensuring that they are not mistakenly miss-classified as Spam.
While it is advantageous for as many issued email addresses as possible to contain a valid Message Key, it is not necessary for all instance or issued email addresses to contain a valid key. Conceptually, Message Keys are only used to prevent a false positive, and the absence of a key should not increase a messages likelihood of being classified as Spam.
As we have seen in the proceeding passage, Message Keys take many forms, but the underling purpose is to carry a unique code or key which can be used to connect incoming messages with issuing events.
The reason why there are multiple forms of Message Keys is to optimize the likelihood of preservation of the key while presenting the email address in a form compatible with the intended method of acquisition.
-
How email addresses are acquired by the sender.
Everyone has an email address, but do they have your address? If so, then how did they get it? Unlike your house keys, you give your email address out to everyone. You put it on your business card, you email it to a friend, who forwards it to a mutual friend, but typically and most frequently you distribute it insentiently – as it goes out in every message that you send.
There are of course other ways that people acquire your email address. Following is a brief summary of each method along with the preferred form of Message Key that is best suited for distribution via that method.
-
Acquired from a received email
The most common method whereby people acquire an email address is from an email that they receive, either directly from the protected user, or via a third party. Typically one of the first things that a user does when they change their email address is to email it to all of their friends. Once received, the email address will generally be added to the recipients address book.
Preferred form of key: DNA/CaseKey Hybrid Key
-
Acquired from a web page
While it is fairly uncommon now days to see an email address published on a web page, many users still prefer to send an email then to fill out a web form. Accordingly, the mailto tag is still featured on many sites, and the mailto tag still accounts for a significant number of first contact messages.
Preferred form of key: Tagged Addressing/CaseKey Hybrid Key, if the protected users mail system supports it, otherwise a CaseKey
-
Acquired via a web form
The second most popular acquisition method is via a web form. This includes signing up for social networks, email publications, newsletter Subscriptions, and other services where an email address is required to be entered in to a web form.
Preferred form of key: Tagged Addressing/CaseKey Hybrid Key, if the protected users mail system supports it, otherwise a CaseKey
-
Acquired off-line, via phone, business card, etc
Typically off-line acquisition involves the sender manually typing in the protected users email address. For example: from a business card, over the phone, or from off-line media. Direct “typing in” of an email address is error prone and unreliable – so users tend to avoid it. Accordingly the proportion of first contact messages that contain manually typed in email addresses is very low.
Preferred form of key: Tagged Addressing Key, if the protected users mail system supports it.
-
Message Key Issuing Facilities
New Message Keys are randomly generated and issued from a key issuing facility. The embedded codes of new keys are recorded along with the details of their provisioning. These details may include: issuing facility, key form, time, and expiry date, and if known, who the key was issued to.
It can be seen from Figure 1 that there are three different types of key issuing facilities, each capable of issuing different forms of keys, and each positioned to reduce one or more types of false positives.
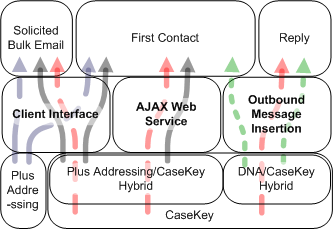
Figure 1: Each type of issuing facility targets one or more particular types of false positives.
The types of key issuing facilities are designed to cater for each of the acquisition methods that were described previously, and are as follows:
- Outbound Message Insertion,
- AJAX Web Service, and
- Manual Key Issuing Facility (Client Interface)
-
Outbound Message Insertion
The purpose of the Outbound Message Insertion module is to intercept all out going messages and to embed Message Keys in to all instances of the protected users email address.
Usually implemented at the out bound SMTP gateway, its implementation is relatively easy and simple, requiring no user interaction, and no user interface.
Typically inserts DNA/CaseKey Hybrid Keys, but if high speed in place stream insertion is required, then may insert only CaseKeys.
-
AJAX Web Service
The purpose of the AJAX Web Service Key Issuing module is to dynamically insert a “message keyed” instance of the protected users email address in to the contents of a web page typically within a mailto tag.
While it may be unadvisable to publish an email address on a web page, users still do it. If the user must publish their email address then at least by inserting a Message Key we can guarantee delivery of legitimate messages that flow from it. This service also gives us the opportunity to include obfuscate techniques to at least make the address as difficult as possible to harvest.
Message Keys that are published on web pages should be set to auto-expire – after a relatively short period such as 3 days. The AJAX service should automatically cycle the Message Key for a web site on a daily basis – one new unique key would be issued each day. This allows the site visitor 3 days to use the CaseKey before it expires.
This works because the nature of usage of an “on-line published” email address is that the address will be used at the time of issue. A user will click a “mailto:” link and typically send the message within a few days at the most. However, Spambots take time to harvest messages, sell the lists, and finally send the spam sometime later, by which time the CaseKey has expired.
Message Keys do not block Spam, they detect false positives. Even if the user were to keep the CaseKeyed email address and to use it after it had expired then their message would be no worse off than if it was sent prior to implementation of the Message Keys system. On the other hand however, Message Keys technology will ensure that for users who do send before the Key Expires, that their message will not be mistaken for spam.
Note: In user feedback dependant systems Message Keys that are set to auto expire should be excluded from is not Spam voting and their use should be limited to ensuring that a message is not placed in the user’s Spam folder.
Typically issues Tagged Addressing/CaseKey Hybrid Keys, if the protected users mail system supports it, otherwise a CaseKey.
-
Client Interface
A manual ad-hoc Message Key issuing facility is required to facilitate the use of Message Key embedded email addresses with Web Forms and for off-line uses such as printing on business cards.
Ideally such a facility will allow the user to indicate the purpose of the key, and will issue the address encoded in an appropriate form for the indicated purpose.
-
How Message Keys Help
Message Keys are used to match an incoming message with an email address issuing event. This information can then be used by Spam Filters to identify legitimate messages that may have otherwise been mistaken for Spam, and thereby improve the filter’s false positive rate.
In systems that benefit from user feedback, Message Keys automate the “Is not Spam” button which helps in two ways.
-
Firstly, it identifies messages that would otherwise be false positives, and
-
Secondly, it provides the feedback required to dynamically train the filter in real-time.
One problem with user feedback systems, particularly successful ones, is that their users may not check their Spam folders very often and this can result in the effectiveness of the filter degrading. Message Keys address this issue by providing timely automated feedback.
-
How Message Keys Reduce First Contact Lost Messages
Typically first contact email addresses are acquired via either, a web page, a web form, an email, or typed-in from a business card. As described above Message Key Issuing Facilities are provided to cater for each of these acquisition methods. Specifically, these facilities are as follows:
-
Outbound Message Insertion,
-
An AJAX Web Service, and
-
Manual Key Issuing Facility
-
How Message Keys Reduce Reply Lost Messages
Replies are the most common form of email message and fortunately Reply Lost Messages are the easiest to avoid.
 The Outbound Message Insertion module as described above intercepts all out going messages and embeds Message Keys in to all instances of the protected users email address.
The Outbound Message Insertion module as described above intercepts all out going messages and embeds Message Keys in to all instances of the protected users email address.
The DNA/CaseKey Hybrid Keys that are inserted are particularly robust and are typically preserved when the recipient replies from either the original recipient address or an alternative address, when added to an address book, or when forwarded for use by a third party.
For example, if the protected user sends an email to sales@example.com and the reply is sent from john.smith@example.com then the Message Key would typically be preserved.
-
How Message Keys Reduce Solicited Bulk Email Lost Messages
As described above, a client interface is provided to facilitate the ad-hoc issuing of Message Key embedded instances of the protected users email address in a form that is optimal for pasting in to a web form. If the protected users email facility supports plus or minus addressing then a Tagged Addressing/CaseKey Hybrid key may be issued, subject to the user being aware that in the event that the web form does not allow tagged addressing, that the Tag may need to be removed.
Alternatively, the default behavior may be to issue a plain CaseKey only, with an option for the more sophisticated user to select a Tagged Addressing/CaseKey Hybrid key as required.
-
How Message Keys Enhance User Feedback Dependent Systems
How: By automating the is not Spam button Message Keys recover lost messages, and remove user dependency, thereby maintaining user confidence.
-
User Trust Oscillation
While user feedback dependent systems have proven to be very effective in identifying spam, they are limited by their user’s tolerance to lost messages.
With reference to Figure 2 below, the blue line represents the systems lost message rate in a typical user feedback dependent system, while the dotted orange line represents the users false positive tolerance threshold. As can be seen from the graph, the systems lost message rate is bound to the users false positive tolerance threshold and will oscillate around it.
Figure 2: Impact of CaseKeys on User Confidence
This is because, once the system achieves a sufficiently low lost message rate to secure the user’s trust, then “Is not Spam” votes plummet, resulting in the degeneration of the system to the point where the user’s trust is withdrawn and “Is not Spam” votes return to their previous levels. The cycle then repeats with the unfortunate side effect being that the system fails to exceed the user’s tolerance threshold 50% of the time.
Message Keys enhances the operation of a user feedback dependent system by producing high volumes of high quality “Is not Spam” votes. “Message Key” votes are of several orders of magnitude larger in volume, and more detailed and reliable than human votes. Message Key votes identify who the unique key was issued to (the recipient’s email address), when it was issued, and where it was issued (in a sent message or web page appearance). This allows the user feedback dependent System to weigh the value of the vote, facilitating an increase in the sophistication of the filter’s algorithms. A Message Key Enhanced System also provides equal treatment for small domains which typically carry a high proportion of business to business messages, and have been historically disadvantaged in the past.
Removing the reliance on the user to identify false positives has other benefits as well – such as dramatically increasing the systems response time, and maintaining a higher level of user satisfaction and confidence. Typically, the lost message rate as indicated by the magenta line in the proceeding graph can be maintained at a level where almost all users cease checking their Spam folder. To these users, Spam is no longer an issue – it is a thing of the past.
-
How Message Keys Enhance DNSBL usage
How: By keeping false positives to a minimum, Message Keys allow the use of a more aggressive list criterion, thereby maximizing the proportion of messages that can be blocked at the SMTP Gateway.
DNS Black Lists or combinations of DNS Black Lists can provide a very efficient method for blocking large proportions of Spam. Typically over 90% of incoming Spam can be identified from the originating IP Address alone. Being IP based, connections can be refused or severed before the message is fully received, thereby avoiding bandwidth consumption and CPU cycles of content filtering.
The down side is that to reach this level of detection a fairly broad list criterion will need to be employed, and unfortunately broadening the list criteria generally increases the likelihood of list false positives, and being IP based once a mistake has been made then usually all messages from the same sender will be blocked repeatedly. In addition, due to the sheer quantity of Spam messages that are typically blocked, the blocked messages are often rejected or discarded rather than stored in the users Spam folder. These measures combine to make discovery of lost messages difficult, if not impossible.
However, Message Keys in either the envelop or message headers can be used to identify legitimate messages before the entire message has been read from the wire. Further automated feedback on recovered messages can be provided to the list provide to assist with list maintenance.
-
Invalidating Compromised Keys
Compromised Message Keys are invalidated by the is Spam button. Should a key be compromised by a Spammer and used to circumvent the Spam Filter, then the message would appear as a false negative in the users inbox. Should this occur then the user indicates the message is Spam via the is Spam button in the usual way and the compromised key is automatically invalidated.
-
Implementation Architecture
While actual implementation will vary depending on the existing email systems architecture, conceptually a Message Keys system works by inserting keys at one or more insertion points, and then monitoring the existing filters Spam Determinations for the presence of valid keys and recovering any false positives as necessary.
-
Minimal Implementation
A minimal implementation requires only two components – an Outbound Message Key Insertion Module, and a Spam Folder Monitoring Module.
Such a system will issue only a single key form DNA/CaseKey Hybrid keys, and will provide no user interface. This basic system runs independent of the user and apart from satisfying users curiosity there is no user training required.
The advantage of a basic system is that it is very quick, easy, and inexpensive to implement. On the other hand the disadvantage is that it primarily only addresses Reply false positives, and to a lesser extend a significantly smaller proportion of First Contact false positives, with the expected recovery of Solicited Bulk Email false positives to be negligible.
-
Full Implementation
A full implementation requires each of the following functional components:
-
Outbound Message Key Insertion Module,
-
Spam Folder Monitoring Module,
-
An AJAX Web Service, and
-
Manual Key Issuing Facility.
The advantage of a full implementation is that it reduces a very high proportion of all types of false positives, including First Contact false positives, which are arguably the most challenging type of false positive to avoid, and are also those which causes the user the most pain. In addition, a full implementation is likely to reduce the lost message rate to a point where the user no longer routinely checks their spam folder, thereby greatly increasing the value of the filter to the user.
-
Scalability
-
Bandwidth
-
When implemented according to the preferred configuration where DNA/CaseKey Hybrid Keys are being inserted in to each outbound message, then the Message Key adds approximately 50 bytes per message. Alternatively, when implemented as CaseKey insertion only, then zero extra bytes are required.
-
Data Storage
While the specific requirements of each implementation may vary, the following may be used as a rough provisioning guide.
-
Keys per User: 50
-
Data per Key: 50 Bytes
-
Storage per User: 2.5KB (50x50B)
-
Total Storage per Million Users: 2.5GB (2.5KBx1M)
-
Data Storage Contention
Although the degree of database contention is largely implementation dependant, database contention should be minimal for the following reasons:
-
Only incoming messages that both contain a key and that have been classified as Spam result in a database read request,
-
The proportion of outgoing messages to incoming messages is very low, and the vast majority of outgoing messages will only result in a database read request, and
-
While Initial Contact outgoing messages do generate a database write, the proportion of Initial Contact messages is minimal as the vast majority of messages will be to recipients that have already been issued a unique key.
-
Benefits to End Users
Message Keys provide significant benefits to the end user, which include:
-
Dramatically reducing a users exposure to spam.
-
Reclaiming time that is currently lost by the user reviewing their Spam folder and looking for lost messages.
-
Restoring confidence, alleviating fear, frustration and spam related stress.
-
Optionally the user can be alerted each time that a lost message is found reassuring the user that the system is working and maintaining the perceived value of the system form a users perspective.
Initially, the primary motivation for new users to use the system is the fear of not knowing which messages are being lost. It is the same fear that drives them to periodically check their junk folders. How many messages did your spam filter loose today? The sustained value proposition however goes beyond the value of the lost messages themselves, and includes the flow-on benefits of reclaiming the time that is currently lost looking for lost messages and eliminating their exposure to spam.
-
Effect on User Loyalty
In addition to the benefits of a reliable email system, a Message Keys enabled system provides a unique incentive for a user to maintain the same email address. This is because as they use the system, unique keyed instance of their email address are distributed throughout their social and professional networks. Should the user then change their email address, then they would lose the benefit of this investment, as it would take considerable time for these keys to be replaced – during which time they would forgo the protection offered by the Message Keys enabled system protection that, by this stage they would recognize the value of.
-
Early Return on Investment
Typically the first incoming messages to contain valid Message Keys will be replies to message that were sent after the Message Key system was first activated, so reduction of Reply lost messages is almost immediate.
First Contact lost messages are also almost immediately eliminated as the protected user utilizes the key issuing facilities described earlier.
Finally Solicited Bulk Email lost messages reduce over time as the protected user utilizes the key issuing facility to register for social networks, email publications, newsletters, and other services where an email address is required.
-
User Acceptance
Perhaps the most significant benefits of a Message Keys enabled system, is that it provides additional identifiable value to the end user. Introducing the user to the system in a manner that focuses on these end user benefits will assist with user acceptance.
The following is an example on introductory email that could be used to inform users of the implementation of the Message Keys System.
The notice would go something like:
“In an effort to serve you better, improve your online experiences and protect you from lost messages, we have partnered with Geobytes to provide our users with a Message Keys facility. In the near future, replies to your messages will be protected by Geobyte’s Message Keys technology, and are thereby much less likely to get caught in your Spam Filter’s junk folder. Go to www.keycustodian.com to find out more.”
The following is an example of a footer that may optionally be appended to the end of outbound email from participating users.
Replies to this message are protected by Geobytes’ Message Keys technology, and are thereby guaranteed not to get caught in my Spam Filter’s junk folder.
Preferably, users should be allow to opt out at anytime to avoid the footer, or could perhaps upgrade to a paid subscription if they wanted to be able to customize or remove the contents of the footer.
-
Reduced Support Costs
Message Keys are a spam filter companion technology. They help spam filters work better, which results in higher levels of user satisfaction and less calls from angry users who have just discovered that their spam filter has lost an important legitimate message.
Message Keys do not identify spam they only identify messages that have been incorrectly processed as spam, therefore the user can embrace or ignore the system to whatever extent that they feel comfortable with and still be no worse off than they were prior to the integration of Message Keys.
-
Conclusion
- The practical value of a Spam Filter is in its ability to reduce a user’s exposure to Spam. Only when a user’s confidence is maintained at a sufficiently high level that they no longer check their Spam folder, is their exposure to Spam eliminated.
- Users check their Spam folder – exposing themselves to all of the Spam, because of their fear of false positives. Each time that they find a false positive, their fear is justified and their confidence falls a little further.
- Message Keys function as a “security pass” by matching an incoming message with an email address issuing event. This information can then be used by Spam Filters to identify legitimate messages that may have otherwise been mistaken for Spam, and thereby improve the filter’s false positive rate.
- Message Keys reduce all classes of false positives. First Contact, Reply, and Solicited Bulk Email false positives can all be almost entirely eliminated.
- For systems that benefit from user feedback, Message Keys provide the is not Spam feedback in place of the user, allowing the system to maintain user confidence.
- Currently, all Spam filters suffer from false positives. Whatever a filter’s false positive rate, the integration of a Message Keys System will reduce it further by identifying messages that would otherwise be routed to the Spam folder.
- A Message Keys enabled system provides additional identifiable value to the end user such as the ability to know how and when someone acquired their email address.
- Finally, exposing a user to spam in their Spam folder is still exposing the user to Spam, and the best way to avoid this exposure is to avoid false positives. Fewer false positives result in happier users, fewer support calls, and less churn.
1 Ferris Research (2003) estimates that blocked legitimate email, or false positives, cost U.S. businesses roughly $3.5 billion in 2003 alone.
2 Repeated for emphasis.
3 Lyris’ Content Checker (http://www.lyris.com/contentchecker) tells you how your e-zine ranks in Spam Assassin
4 Google Alerts are an automated email service containing Google search results based on a predefined query or topic. http://www.google.com/alerts
5 DomainKeys Identified Mail (DKIM) is a method for associating a domain name to an email… The value is placed in the DKIM-Signature: header field. http://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
6 Sender Policy Framework (SPF), as defined in RFC 4408, is an e-mail validation system designed to prevent e-mail spam by tackling source address spoofing, a common vulnerability. SPF allows administrators to specify which hosts are allowed to send e-mail from a given domain by creating a specific SPF record in the public Domain Name System (DNS).
7 Some mail servers violate RFC 5322, and the recommendations in RFC 3696, by refusing to send mail addressed to a user on another system merely because the local-part of the address contains the plus sign – http://en.wikipedia.org/wiki/Plus_addressing#Address_tags
8 Using various separators between the base name and tag are supported by several email services, including Runbox (plus and minus), Google Mail (plus), Yahoo! Mail Plus (minus), and FastMail (plus) http://en.wikipedia.org/wiki/E-mail_address#Plus_.28or_Minus.29_addressing
9 “Normally, a mailbox is comprised of two parts:
- an optional display name that indicates the name of the recipient (which could be a person or a system) that could be displayed to the user of a mail application, and
- an addr-spec address enclosed in angle brackets (“<” and “>”). ” http://www.faqs.org/rfcs/rfc2822.html

